Product
Products
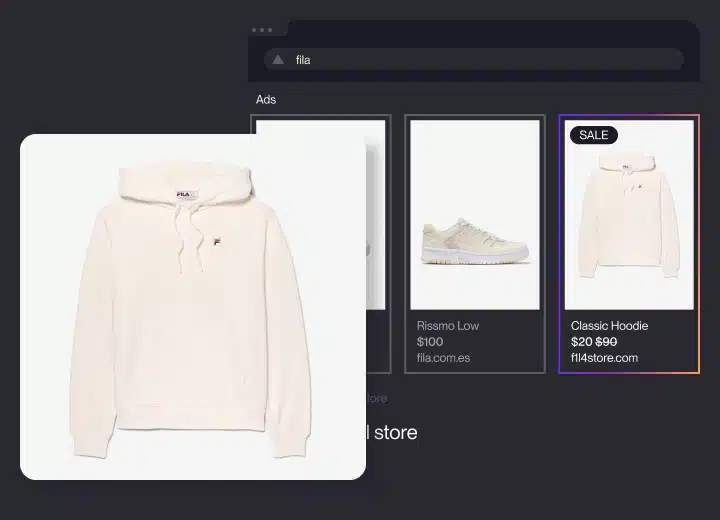
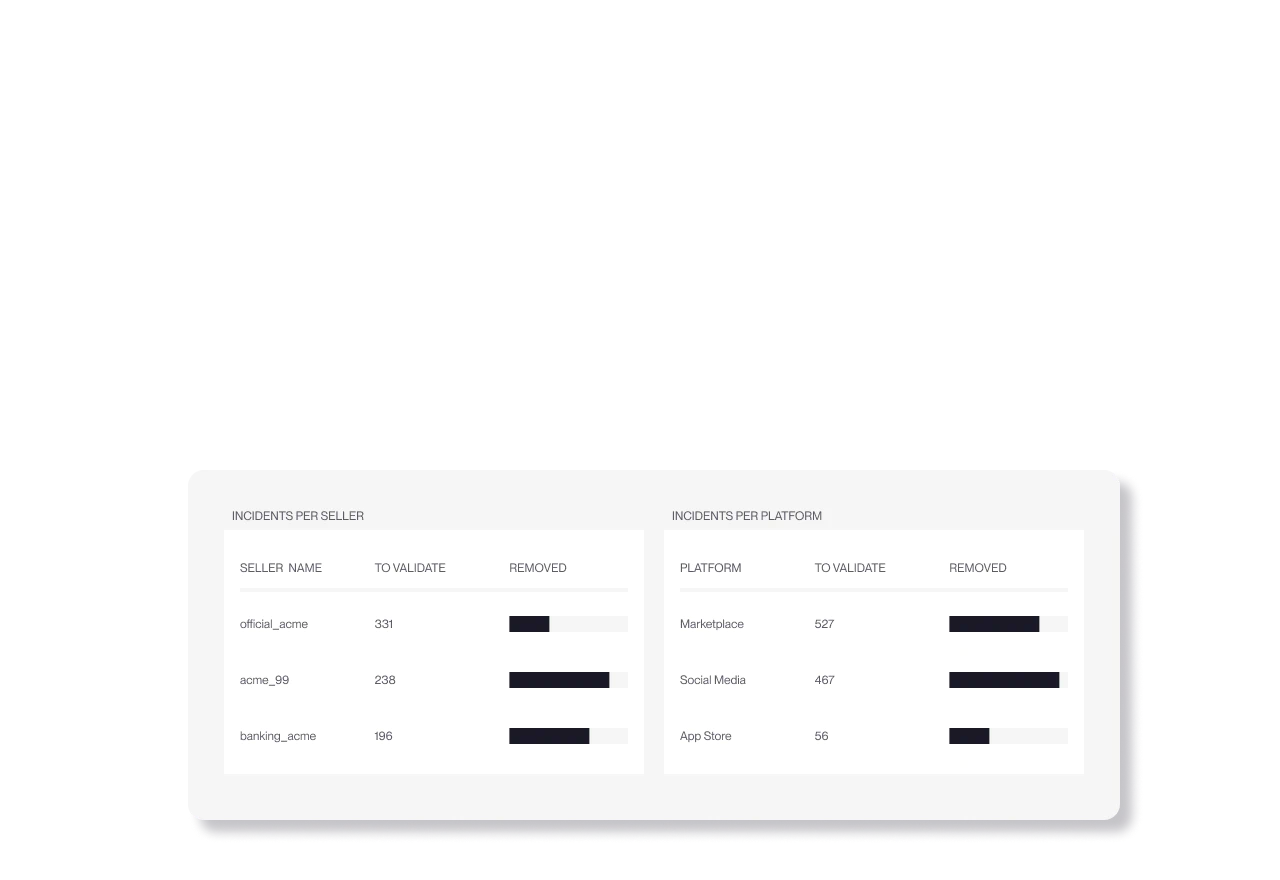
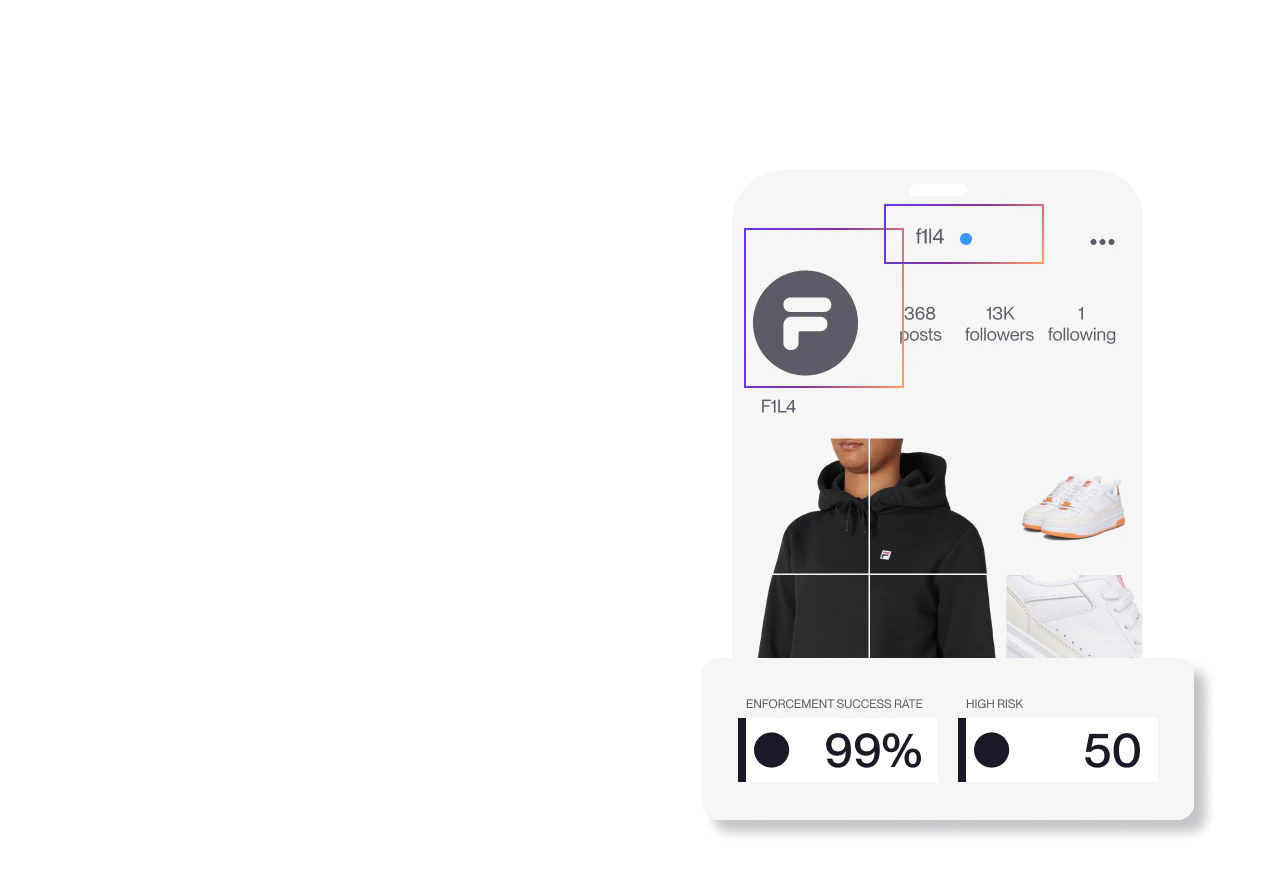
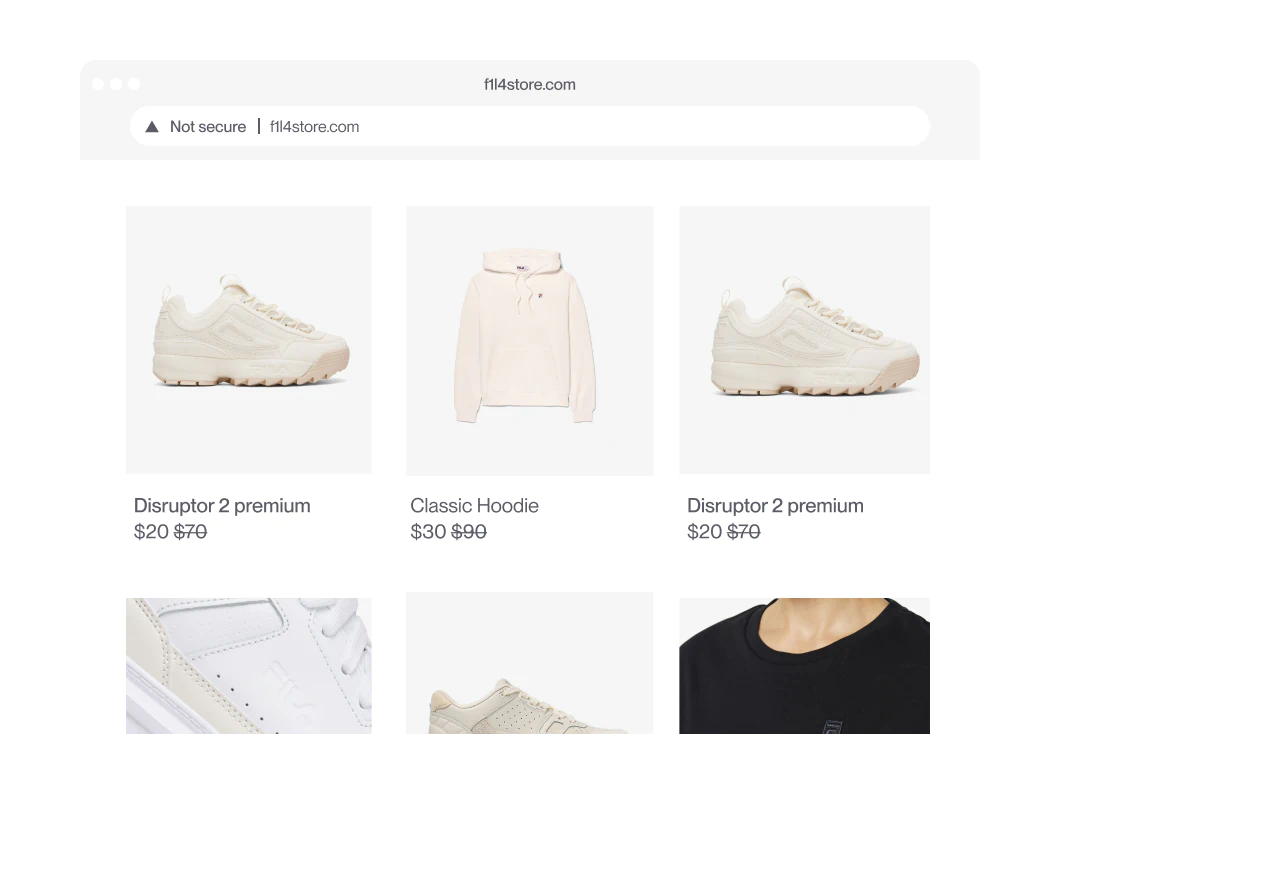
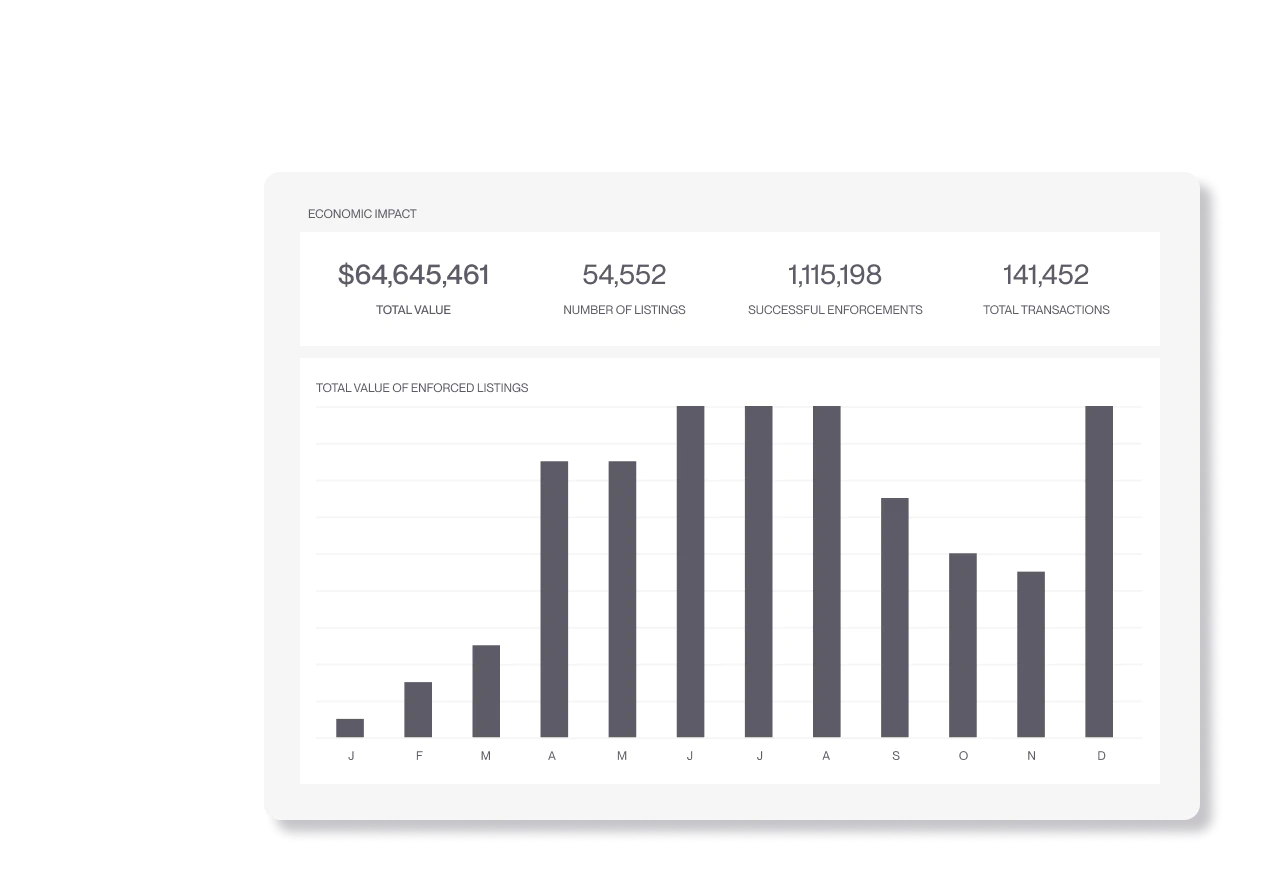
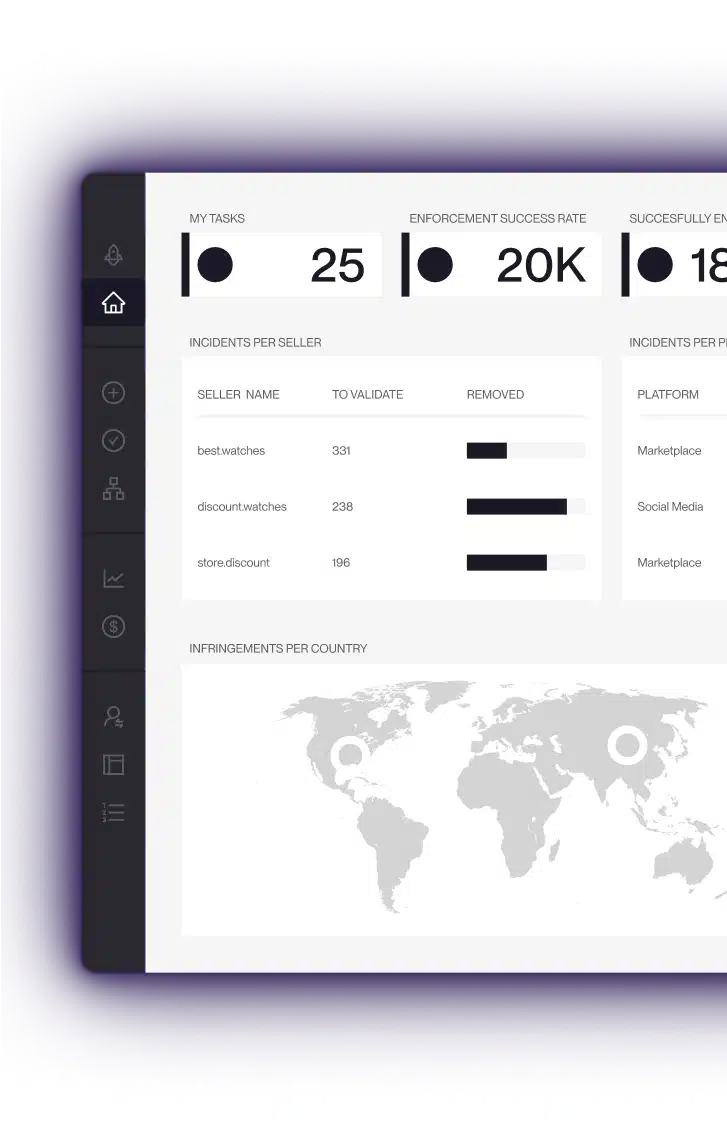
Brand Protection
Remove counterfeits across marketplaces, websites, social media, ads, and more
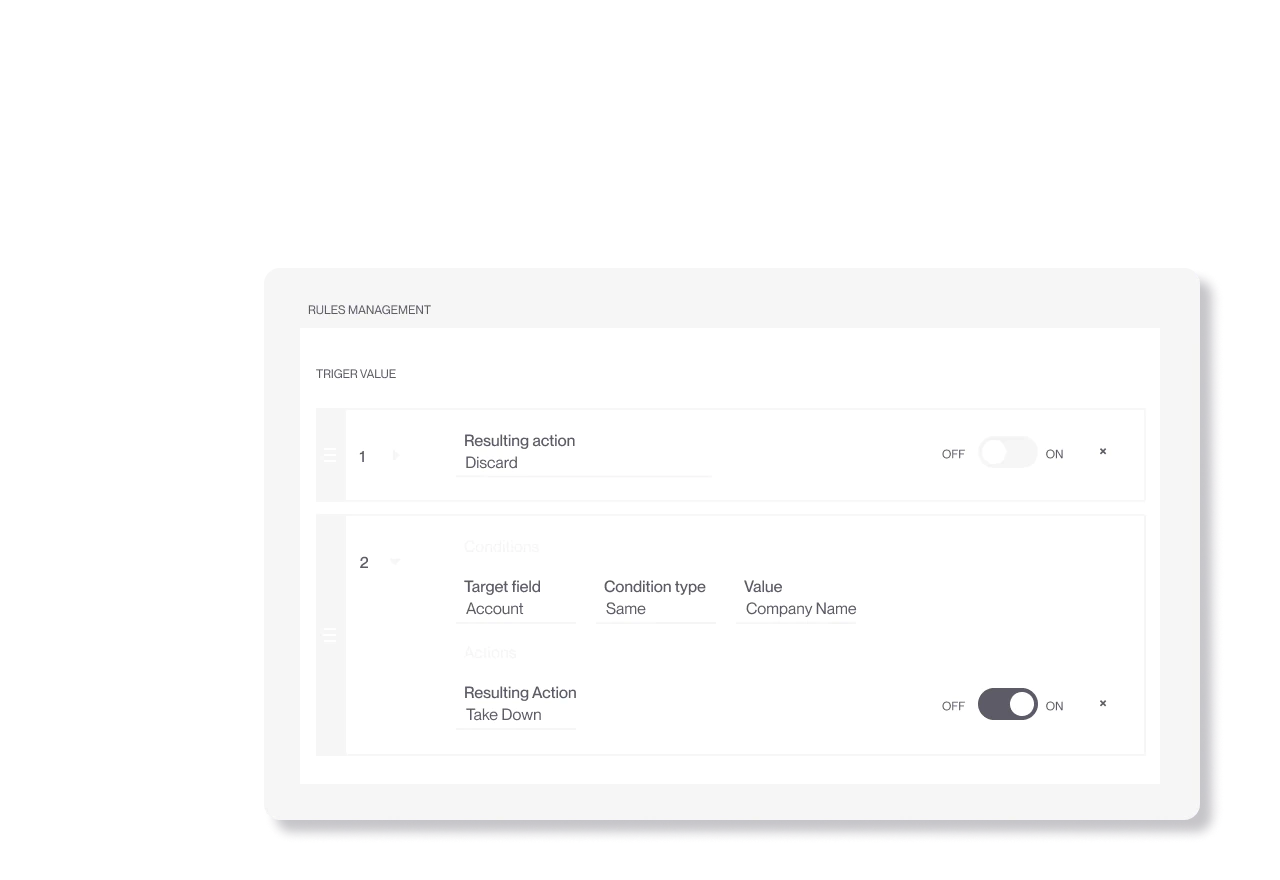
Anti Piracy
Cut access and remove illegal content at scale
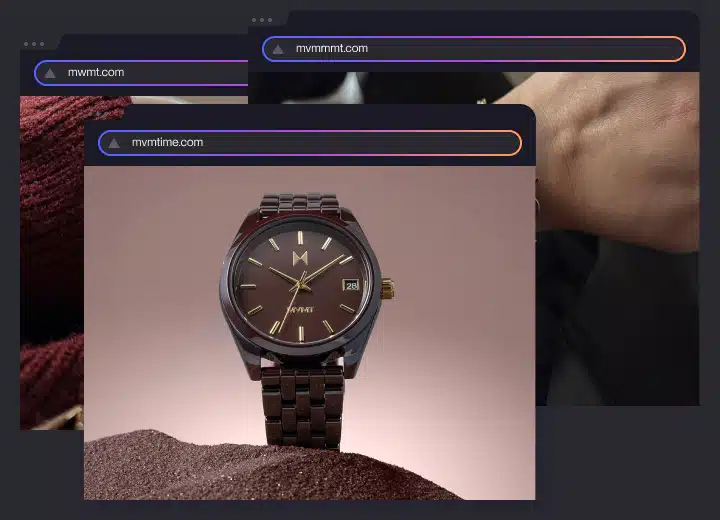
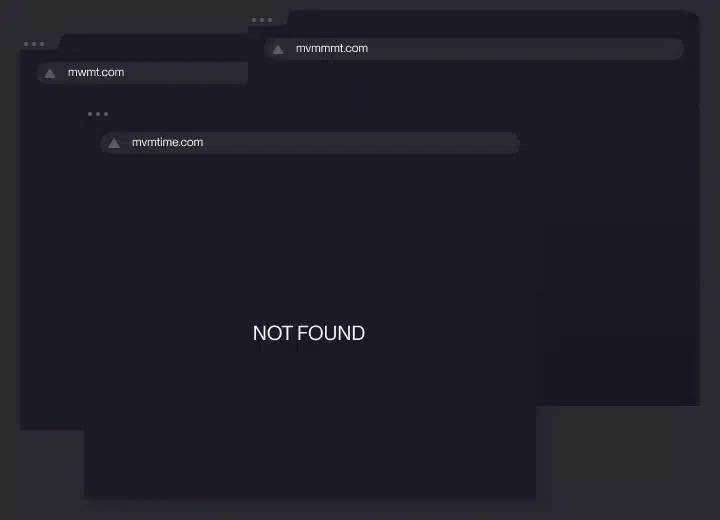
Domain Management
Detect, monitor, and reclaim domains misusing your brand
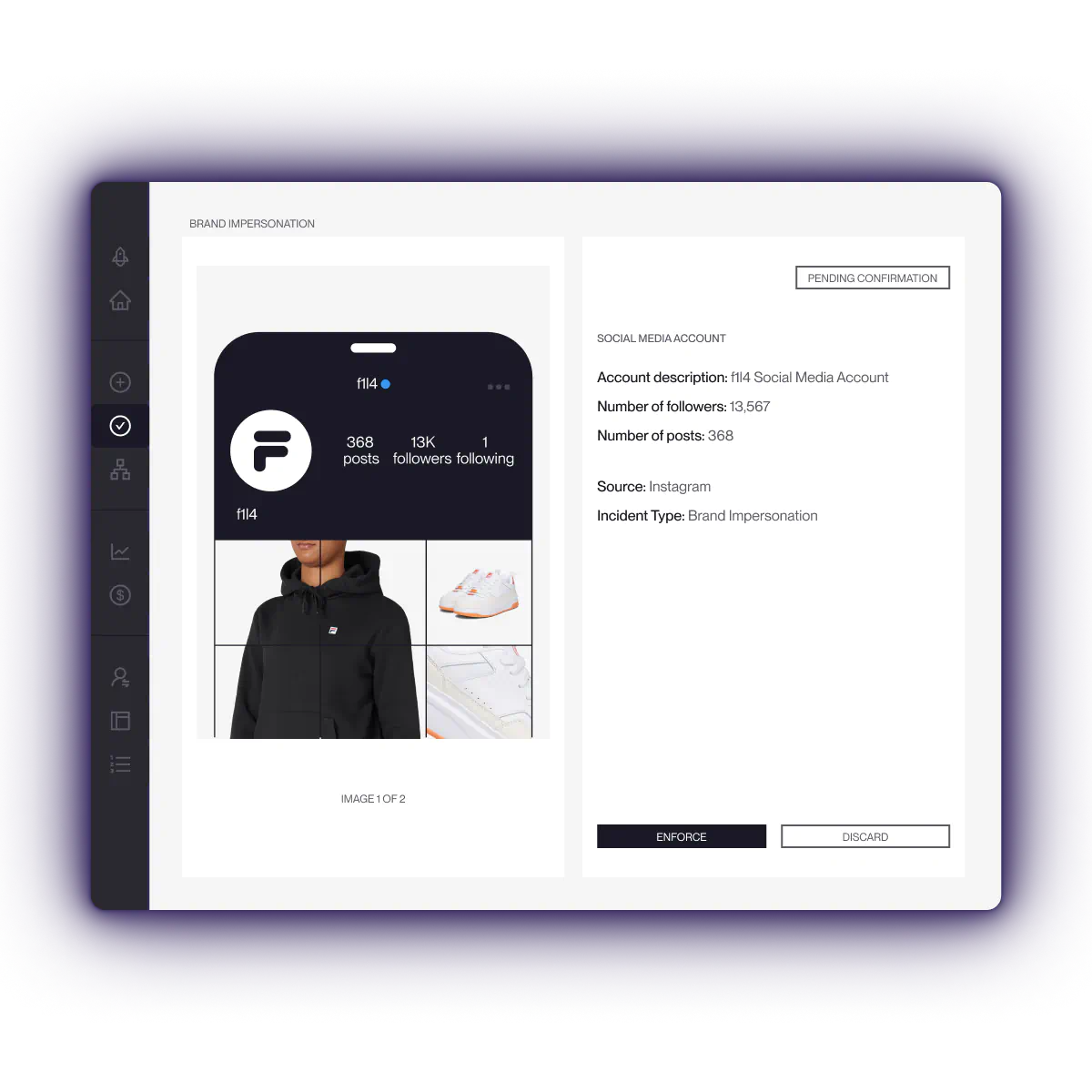
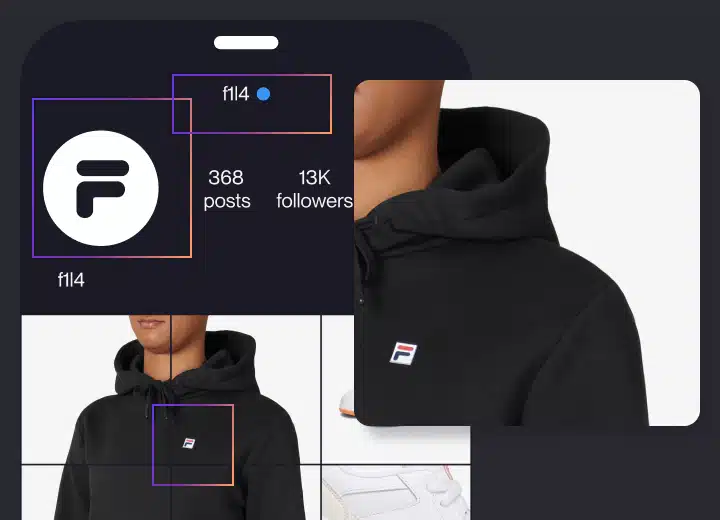
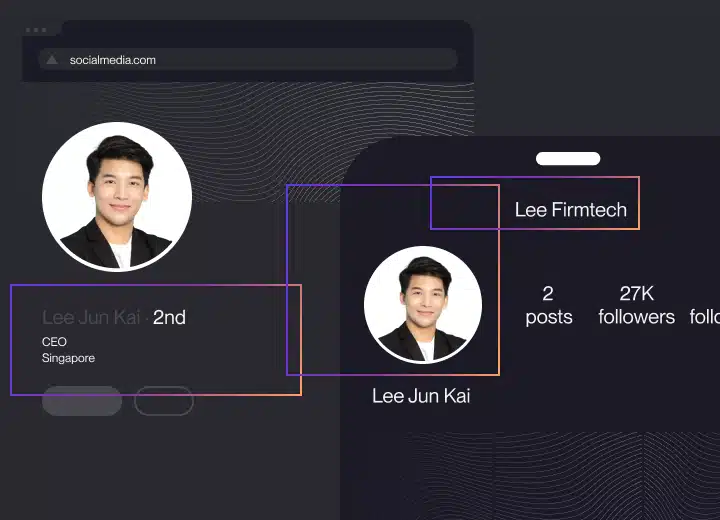
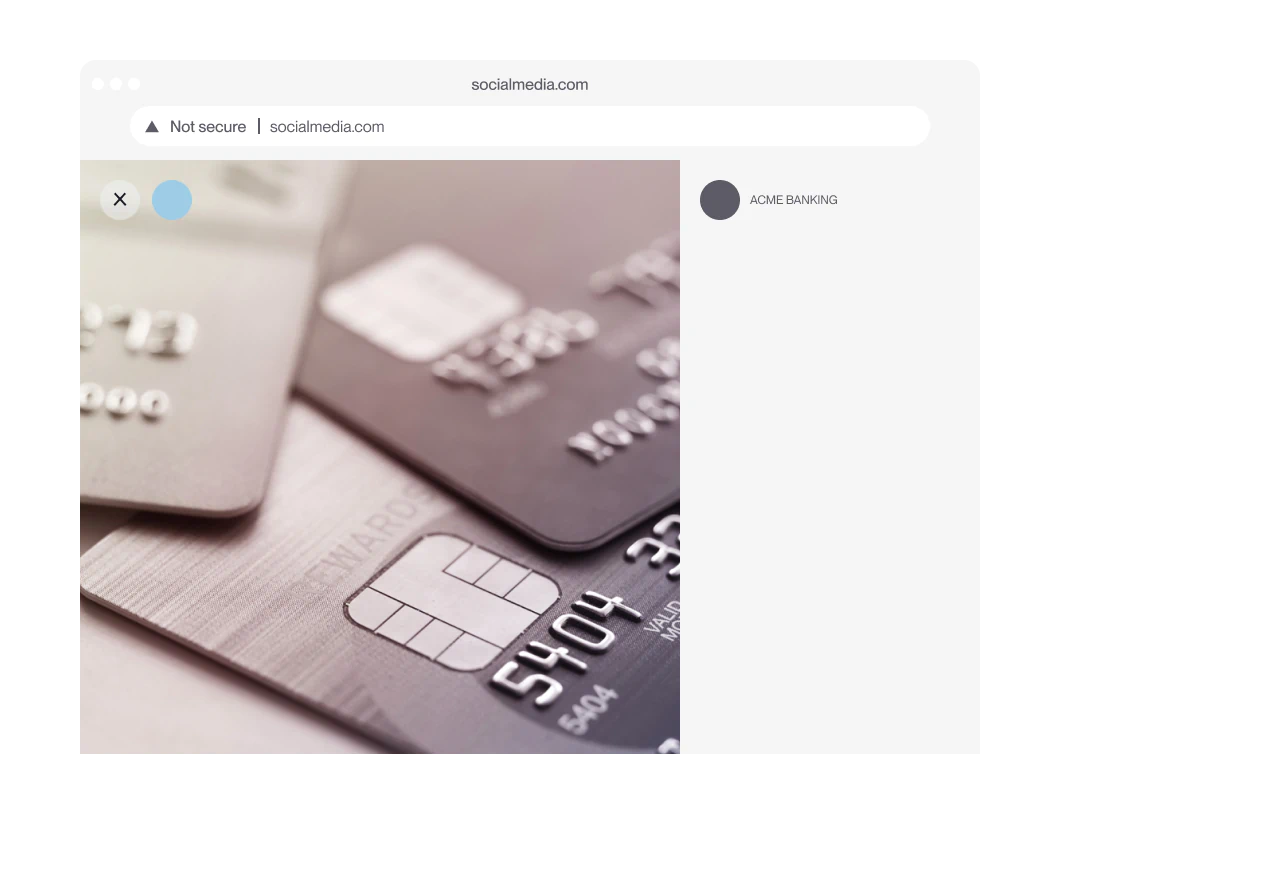
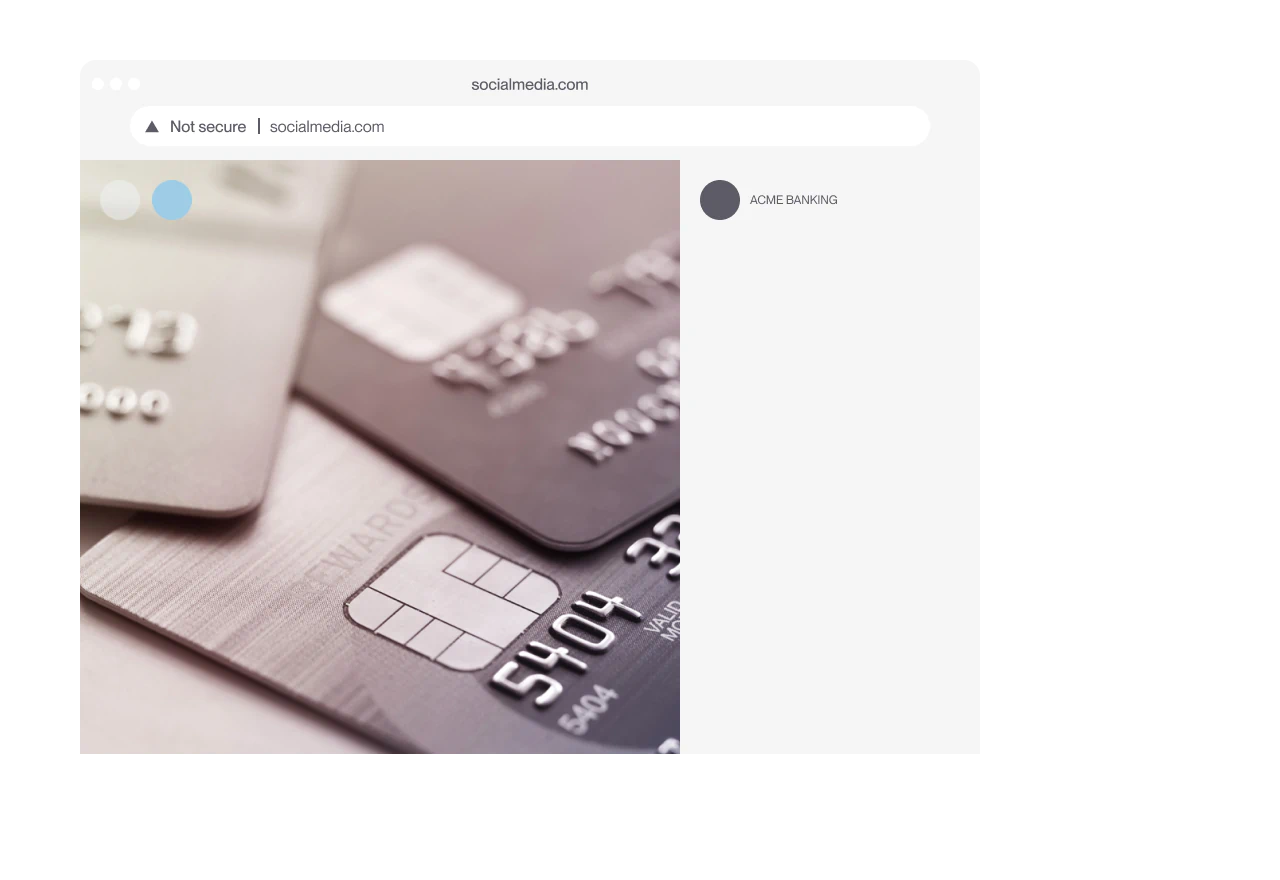
Impersonation Removal
Remove fake sites, profiles, and ads before they damage your brand
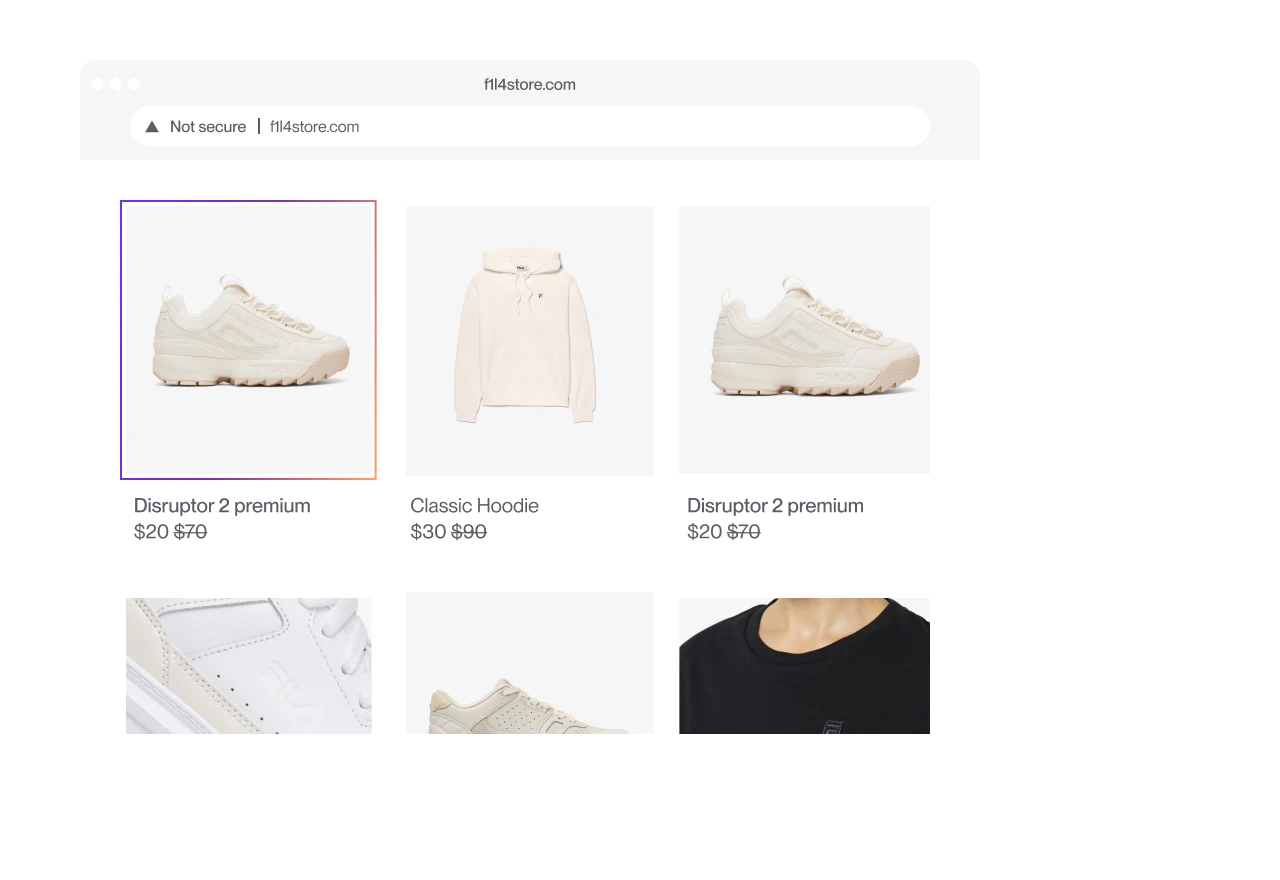
Gray Market
Block unauthorized sellers and parallel imports
Social Video Growth
Protect your video content and monetize it on social platforms
Revenue Recovery Program
Permanently remove sellers and recover revenue with zero-cost litigation
Apply now
Ready to see Red Points in action?
Request your demoRefer a Business
You get up to $10K and they get 1 month free
Learn more
Coverage
Coverage
Use Cases
Pricing
Clients
Company
Resources